
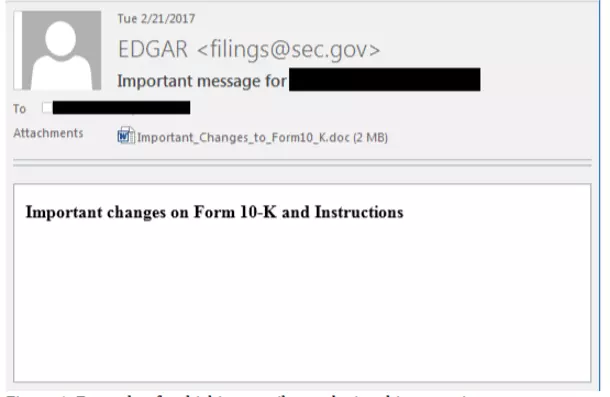
It appears to be innocent and routine. The CFO of your company forwards to you an urgent-sounding, personally addressed email from the Securities Exchange Commission’s EDGAR public filing system announcing changes to the reporting system. Last week you signed the attestation of the accuracy of your Quarterly Report on SEC Form 10-Q. You hope you have not made a mistake or missed an important change. You look over the email again. At first glance it appears legit:
Or it might be your worst nightmare: an email from the SEC questioning your firm’s disclosures, revenue recognition treatment, or internal controls on access to non-public information. The Commission Seal looks imposing. The email attaches an official-looking Word document requesting some basic information. It all looks real. You decide you better open the attachment and plan your response.
Turns out, it’s a fake email —not from the SEC at all but from an impostor. (It’s likely from a criminal syndicate in Eastern Europe seeking access to your network to gain access to material non-public information in order to profit from stock trades guided by access to inside information.)
On March 7, 2017, Fortune magazine reported that a number of public companies received well-crafted but bogus emails that appeared to announce regulatory compliance changes from the Securities and Exchange Commission (SEC). According to Fortune, FireEye (a security company) intercepted suspicious emails targeted at companies in sectors ranging from transportation to banking to retail. FireEye reports that numerous company officials opened the Microsoft Word file attached to these emails and exposed their networks to insidious malware.
Opening the Word attachment granted the intruders wide access to internal corporate networks. The attackers’ gambit is a classic example of “spear-phishing"—emails from an apparently legitimate source directed to specifically identified and targeted people likely to receive the type of communication involved. Here the emails were sent to readily identifiable corporate officials with responsibilities relevant to SEC reporting. It might be unusual but not surprising for these corporate officials to receive regulatory reporting change announcements from EDGAR.
Sophisticated efforts to gain access to networks unabashedly co-opt governmental imagery. The example here was directed to public companies subject to SEC reporting requirements, but for private companies, it could just as well be an ersatz communication from virtually any federal, state, or local governmental body.
Mistakes will be made, and other protections to block or evict intruders are certainly advisable, but the first line of defense is always human judgment. Train your management and employees to develop a healthy skepticism of email communications purporting to come from governmental bodies. Some steps that can be taken to avoid these types of scams:
- Assess whether the communication is through normal channels.
- The SEC/EDGAR do not normally send out personally addressed emails to specific corporate officials announcing changes to reporting forms.
- Changes in reporting requirements are not summarily announced. They are widely distributed in the Federal Register and other means for discussion in the financial and accounting communities.
- Assess the form and content of the email itself for any apparent flaws that suggest a scam.
- Compare the display name and email address. The display name is what you see in the “From” field, but it may not be the email address of the sender. An impostor can literally put anything they want in the display name. (In Outlook, right click on the email address in the “From” field, then click “Open Outlook Properties” to see the display name and the email address. Other email applications have similar ways to determine the senders’ email address.)
- Does the Subject “Important” look suspicious?
- The body of the email lacked any meaningful information. Is that normal?
- Most government emails will have a format with confidentiality, email preferences legends, contact instructions for follow-up, and similar legends or footers. Is this email out of the ordinary?
- Look at all the mail servers the email passed through before delivery.
- (In Outlook, open the email, click on the file pull-down menu, then properties, then internet header. In our example, if none of the mail servers appear to be from sec.gov, that’s a red flag.)
- Establish a specific procedure to centralize responses to government announcements and inquiries.
- Independently verify from the source whether the inquiry is legitimate.
Some of these steps may be inconclusive on whether an email is a malicious hacking attempt. It may be difficult to tell if the hacker sent it from their actual email address or if it was spoofed. If it was sent from a hacked email account, it would still look legitimate. We are dealing with sophisticated actors, and things are not always what they seem, so …
… if there is any doubt, don’t trust—and verify.
- Partner
Experience matters. For over 40 years, Glenn Davis’ unwavering commitment to clients has been the delivery of creative and efficient results in dynamic business disputes and cybersecurity challenges. His mission is to provide ...


